In this post, I’l explain how to generate unique and strong passwords for your online accounts.
This topic is especially important if :
You're concerned about online security
You have signed up for many online services
You are reusing the same or similar variants of the same password across multiple sites
Actually, this is the second article from a 6-part series on password management that will be released over the next few days:
Part 1: Why should my password be unique & strong?
Part 2: How to generate unique and strong password
Part 3: Overview of three password managers for iPhone, iPad & Mac
Part 4: How to use iCloud Keychain on iPhone, iPad & Mac
Part 5: How to use 1Password on iPhone, iPad & Mac
Part 6: How to use LastPass on iPhone, iPad & Mac
Recap from my previous post:
The main reasons why online account get hacked are the following:
passwords are either too short or too simple
the same or very similar passwords are reused across multiple accounts
the answers to security questions can be found easily from publicly available information
This is why we need passwords that are unique and strong.
What do you mean by “strong”?
Great question!
Now, let me define what I mean by "strong":
The password should be long enough: minimum 12, preferably 16 characters long (for sensitive accounts)
The password should be made of:
numbers
lower and upper case letters
special characters (+ - , $)
Techniques to create unique and strong passwords
Here I’ll cover 4 techniques:
Padding
Passphrase
Paper-based method
Electronic solution
The padding technique
Strong does not necessarily mean complicated.
For instance, which of those 2 passwords do you think is more difficult to brute-force?
GxQGLg&DjmE8vmy
C4t+++++++++++++
The right answer is 2 because it is one character longer than option 1 (16 vs. 15) and both use at least 1 character of each type (number, lower and upper case letter and special characters).
This technique is called "padding" and consists in using a simple word, changing it a little bit and adding a chosen number of special characters to it, wherever you want to (beginning, end, middle, combination).
Wait a second, Damien!
Didn't you say that we shouldn't use dictionary words and that hackers know very well the most common letter substitutions?
Well spotted!
In this example, password n°2 could indeed be guessed but only if the attacker knew the actual length of your password.
The point I'm trying to make is that it's possible to come up with a long password that is not too complicated to remember.
The risk is that, sooner or later, hackers discover most of our clever techniques (remember those breaches) and incorporate that knowledge into their password cracking tools.
This is why, easy to remember passwords should preferably be used in conjunction with two-factor authentication.
The passphrase technique
In addition to the padding technique shown earlier (with C4t+++++++++++++), you can use the passphrase technique:
You start with a sentence, like: "There are 12 months, 52 weeks and 365 days in a year"
You find a way to compress it to something with at least 12 characters, like "Tr12m,52w&365di@y"
You have a strong password with numbers, upper and lower case letters and special characters
Obviously, you should not use this example, but I hope that you get the philosophy.
It could be a proverb that you like, or an inspiring quote, the title of a song or a dialog in a movie.
For most of the accounts that you have, there is no need to actually remember them and so a randomly generated password is ideal.
But how can we generate them?
Paper-based method
It’s possible to generate random password in an analog fashion, using a paper-based method.
This relies on three main components:
A grid with randomly distributed characters
A strategy for generating complex passwords
A place where you can write down the strategy
First, you'll need to create a randomly generated grid composed of numbers, letters (lower and uppercase) and, if possible, special characters.
The best is to use your own passphrase to generate the grid, so that there is a way to re-create it in the future, in case the grid gets lost.
Obviously, for this technique to be secure, each of us need to have a different grid and the grid must be generated as randomly as possible.
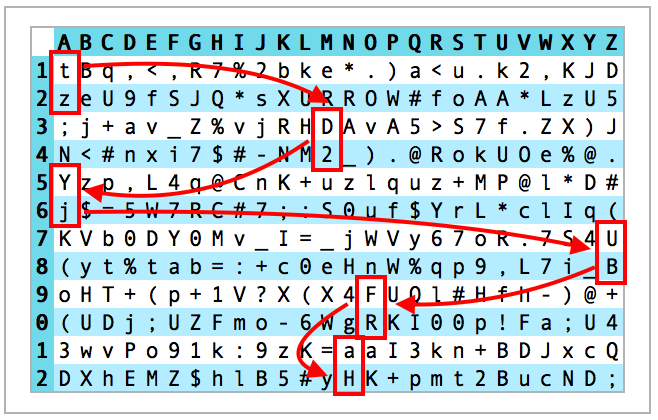
Here is an example of such a grid, generated via the averk.net website.
As you can see, there are 12 rows and as many columns as there are letters in our alphabet.
Once generated, the idea is to print this grid, protect it with a plastic film and keep it with you.
Note: You only need one grid for all the services and this applies both when you signup for the first time and when you'd like to change the password.
The second step consists in generating a complex password for each online service based on a strategy that you define yourself.
Let's take as example the creation of a 12 characters-long password for the Amazon website.
Since the word Amazon is not long enough, there are different strategies that could be used:
Option 1: Use multiple rows for each letter of the word Amazon. In this case, using 2 consecutive rows for each letter would yield a 12-character long password. The input is then AAMMAAZZOONN.
Option 2: Repeating the service name multiple times (in this case, twice is enough). The input is then AMAZONAMAZON
Option 3: Append something to the service name (which could make sense if you have multiple accounts for the same online service). In this case, I'd append my first name (Damien) which would also yield to a 12-character password. The input sequence is then AMAZONDAMIEN.
Let's see the resulting password when going through each letter of the input sequence:
1) AAMMAAZZOONN generates the password tzD2YjUBFRaH
2) AMAZONAMAZON generates the password tR;.l0Keo4aH
3) AMAZONDAMIEN generates the password tR;.l00(XmoH
As you can see, in this particular example, only the second and third strategies generate a strong enough password, as the first one lacks special characters.
It is OK to temporarily write down the password on a piece of paper, but this paper should be shredded or discarded as soon as you're finished signing up or changing your password.
For answers to security questions, you could take the first letter of the associated question and then use the 12 characters for that column.
As an example, if the security question was: "What is the maiden name of your mother?", you could use the sequence of characters underneath the letter "M": eRD2uS_eXW=y
The third, and last step consists in writing down the strategy and have it handy when you need to re-generate the password.
One option could be to use an address book, either physical or electronic, and store the input sequence using the first letter of the online service.
In the Amazon example, the input sequence (i.e. amazondamien) would be written in-between other contacts starting with the letter A.
The big advantage of this method is that it's as low tech as it can be (no need for a computer or mobile device, except to generate the grid the first time).
There are a few drawbacks though:
You need to carry this card with you
It takes time to mentally "generate" the password
If the card gets lost or stolen, it can be a hassle to sort the situation out as you’ll need to:
Re-create the old card to access all your accounts
Create a new card to generate new passwords for all your accounts
Manually change the passwords on all your accounts (as a precautionary measure)
Having said that, this method is a great alternative for people who have a small digital footprint and who have difficulties getting to grip with the electronic method that I'll introduce in the next section.
Electronic solution
With this technique, you'll use software to generate and store passwords electronically.
Even if it's totally doable to use separate tools for each task (generation vs. storage), you will be much better off using only one. No need to copy and paste passwords between different software or systems.
A single application designed to both generate and securely store passwords is called a Password Manager.
At its core, you can see it as an electronic vault encrypted by a strong and memorable password.
Ideally, this password then becomes the only one that you actually have to remember, which frees your memory up.
The biggest benefit of this approach is that you don't need to use similar and/or weak passwords anymore. They can be totally different, as long and as strong as you want.
Another benefit of using a Password Manager is that you can use software (incl. browser plugins) to automatically fill the password for you.
Courtesy from 1Password
No need to even type them. That's a huge time saver!
So, if you can get your head around electronic password management, you'll be both more secure and more efficient filling long and complex passwords.
If you just have one computer or one mobile device, a purely local solution (where the vault only resides on the device) is totally acceptable.
If you're like most people however, then you'll want to synchronise your vault between multiple devices. This, in turn, usually involves passing through third-party servers (i.e iCloud or Dropbox), albeit in a securely encrypted fashion.
To achieve this, there are two main alternatives:
You take responsibility for the conduit which will allow your vault to be synchronised
You let the developer of the Password Manager be responsible for the synchronisation (oftentimes achieved by using a central server for all its customers).
Alternative #1 is in theory the most secure, as it makes a targeted attack more difficult. On the other hand, this means also that you have to remember a second password, in order to gain access to your vault in case something bad happens to your existing device(s).
At this point, you'll probably start having objections in your head, like:
What if somebody intercepts or get their hand on my vault?
What if I forget the password that allows me to open the vault?
These are legitimate questions, no doubt about it, but they entirely miss the point of the benefits of using a password manager, described earlier.
If somebody intercepts or get their hand on your vault, they first need to discover the password that you used to encrypt it.
The best mitigation is to use a long and complex password, yet a memorable one (via the padding or the passphrase technique).
The best antidote to forgetting your main password is to write it down and lock/store it in a safe at home or in the bank.
If you used the passphrase technique, you could, for instance, write the sentence in Apple Notes, then password-protect it (as explained in this post).
In the next post, I'll cover in depth three software solutions, namely iCloud Keychain, 1Password and LastPass.
And you, how do you generate your passwords today?
Please let me know in the comments below!